# Essential Kubernetes Security Tools Every Developer Must Know
Written on
Chapter 1: Understanding Kubernetes Security Principles
Kubernetes security hinges on the four foundational aspects of cloud-native security: cloud, cluster, container, and code. The physical infrastructure that supports Kubernetes forms the backbone of its security in a cloud environment. Therefore, when deploying or configuring a cluster within a data center, it is crucial to follow best practices tailored for Kubernetes security.
When we refer to a “cluster,” we are talking about the various configurable components, including the API and associated applications that comprise it. Naturally, these services need to be established according to appropriate security protocols.
Containers should be developed following optimal design practices, avoiding the use of multiple packages and ensuring the codebase remains as lean as possible by eliminating unnecessary libraries or functions. The code of your application represents a significant attack surface within the Kubernetes landscape. Hence, robust TCP policies should be implemented to safeguard the environment, minimizing the exposure of unused ports and conducting regular assessments.
Kubernetes, due to its microservices architecture, is susceptible to various vulnerabilities, including improperly configured images. Such vulnerabilities can jeopardize user safety. Additionally, flaws in container configurations may expose APIs and other services, granting unauthorized access to the containers.
Tools for Evaluating Kubernetes Security
Numerous tools are available to audit and monitor Kubernetes environments, providing visibility into coding and configuration rules, along with digital certificates that instill confidence in their use. Organizations can invest in these tools with assurance. Let’s examine several key tools for monitoring and assessing Kubernetes security.
ARMO
ARMO’s Kubescape not only conducts security assessments but also compliance evaluations. It analyzes the YAML files of active clusters to identify misconfiguration vulnerabilities early in the CI/CD pipeline, preventing potential issues from escalating. Supporting various established frameworks, including MITRE NSA-CISA, it also allows for the creation of custom compliance templates tailored to specific requirements.
Kubescape seamlessly integrates with CI/CD pipelines, offering compatibility with tools such as CircleCI, GitLab, and GitHub workflows. It provides excellent visibility regarding risk scores, historical scans, and RBAC setups, ensuring that no vulnerabilities go unaddressed following thorough testing. The tool guarantees that all vulnerabilities and compliance violations are remedied before deployment into the cloud infrastructure.
kube-bench
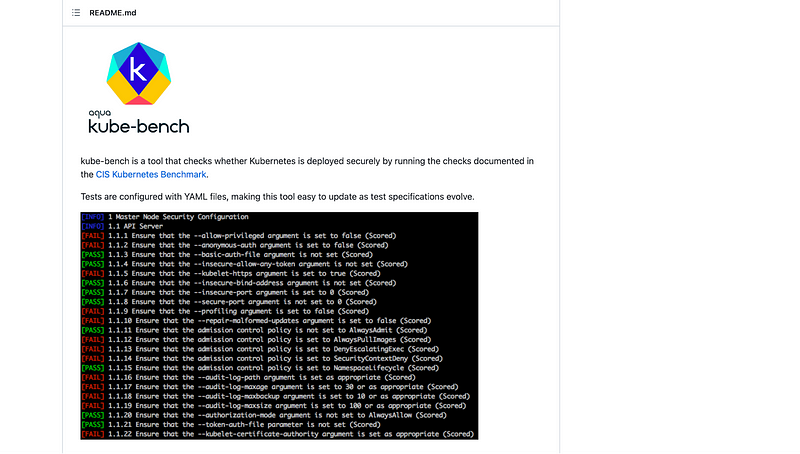
Kubernetes operates within a clustered environment, and kube-bench evaluates deployed clusters to ensure adherence to security best practices and to identify any introduced vulnerabilities. This tool employs various methods for assessment, including operating within a pod.
Initially, the administrator must provide the host’s PID namespace; the tool then identifies the pod to assess and begins its analysis once connected. If all CIS benchmarks have been met, kube-bench will highlight areas needing attention, along with recommendations based on identified issues. Another approach involves running a Kubernetes cluster/EKS within the Amazon Web Services environment.
Terrascan
Terrascan is a static code analyzer for Infrastructure as Code (IaC) that scans for security vulnerabilities. It allows for seamless scanning of IaC and monitors changes to the provisioned cloud infrastructure that could introduce security risks. It also addresses compliance issues, enabling users to identify security vulnerabilities and compliance violations.
Terrascan integrates well with CI/CD processes, helping to mitigate risks before they impact cloud infrastructure. It provides a wide range of security policies and can examine YAML files for vulnerabilities while supporting various platforms, including AWS, GCP, and Azure.
kube-hunter
As its name suggests, kube-hunter is designed to identify vulnerabilities within Kubernetes environments. This open-source security tool is effective for conducting vulnerability assessments on Kubernetes clusters, providing actionable recommendations for organizations to remediate identified issues.
Kube-hunter scans domain or address ranges for open ports and container configurations, mimicking an attacker’s perspective. It can be executed as a container, pod, or on any machine within a cluster, making it effective in both active and passive roles.
Anchore
Anchore focuses on container images, producing outputs based on the CVEs associated with specific software versions used in the Kubernetes cluster. By analyzing container images, it applies custom policies for security assessments. Anchore features whitelisting and blacklisting functions, facilitating the creation of guidelines for settings, passwords, and file content.
To perform vulnerability assessments, Anchore requires container images. If an image is provided, it displays detected vulnerabilities along with their risk assessments. The tool can operate independently or in conjunction with Kubernetes, CI/CD, and Jenkins, allowing administrators to retrieve vulnerability information via the command-line interface (CLI).
Conclusion
As organizations increasingly adopt microservices through Kubernetes clusters, ensuring security becomes essential. This overview has highlighted several tools that can aid in maintaining or enhancing security for Kubernetes environments. However, each tool serves specific purposes, making it crucial for organizations to select tools that align with their unique needs. Moreover, security is not a one-time effort; it is an ongoing process that requires continuous improvement.
Chapter 2: Enhancing Kubernetes Security with Video Insights
The first video, "How to Implement Kubernetes Security at Scale with HashiCorp and SUSE," explores strategies to effectively secure Kubernetes environments across large-scale deployments.
The second video, "Hands-on Hacking Kubernetes and Ways to Prevent It," presented by Eric Smalling from Snyk, provides practical insights into identifying vulnerabilities in Kubernetes and methods to mitigate them.