Phishing Toolkit Enables Creation of Fake Chrome Login Windows
Written on
Chapter 1: Introduction to Phishing Toolkits
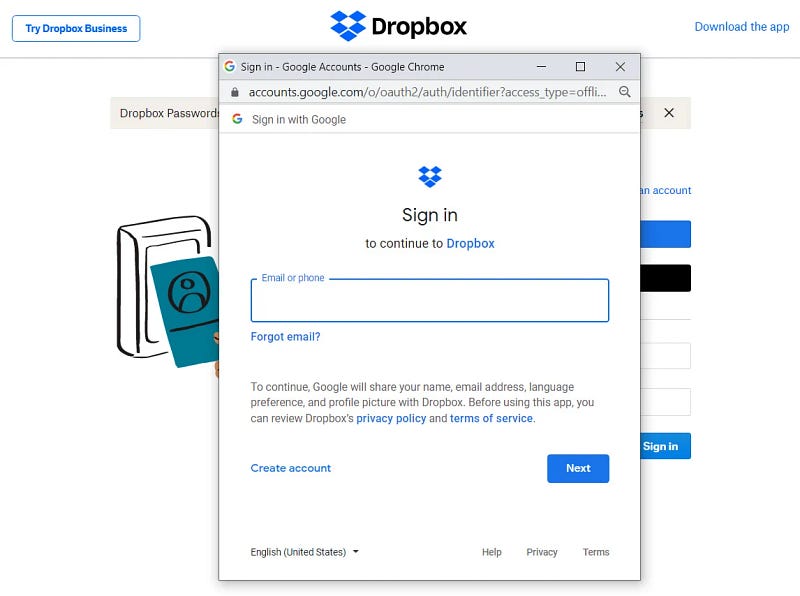
Recent developments have made it easier for individuals to create deceptive Chrome browser windows using a newly released phishing toolkit. Cybercriminals and red team professionals can now craft effective single sign-on (SSO) phishing forms that mimic genuine login interfaces. When browsing the web, you may often encounter options to log in via popular services like Google, Microsoft, Apple, Twitter, or Steam. For example, consider the Dropbox login screen, which allows users to sign in using either an Apple or Google account.
Upon selecting the "Login with Google" or "App" buttons, a browser window designed for SSO will pop up, enabling users to enter their login credentials. These fabricated windows are streamlined to display only the login form alongside a URL address bar that reflects the form’s web address.
This paragraph will result in an indented block of text, typically used for quoting other text.
Section 1.1: The Evolution of Phishing Techniques
Previously, cyber attackers utilized HTML, CSS, and JavaScript to create counterfeit SSO windows, but these often had telltale signs that raised suspicion. Enter the "Browser in the Browser" (BitB) attack method, which employs pre-designed templates to generate realistic Chrome pop-up windows complete with customized URLs and headers for phishing schemes.
By creating fake browser windows inside actual browser environments, this approach effectively enhances phishing attempts. Security researcher Mr.d0x developed these Browser in the Browser templates, making them available on GitHub. The templates cater to Google Chrome on both Windows and Mac, with options for light and dark modes.
Section 1.2: How the Templates Work
According to Mr.d0x, these templates can be easily implemented to create believable Chrome windows that display SSO login forms for any online service. Red teamers can download these templates, customize them with the target URL and window title, and then present the login form using an iframe. Alternatively, they can insert the HTML for the login form directly into the template, although proper alignment requires some CSS and HTML finesse.
Kuba Gretzky, creator of the Evilginx phishing toolkit, recently tested this new method, demonstrating its efficiency with the Evilginx platform. This suggests it could be utilized to capture two-factor authentication (2FA) keys during phishing campaigns.
Chapter 2: Historical Context and Future Implications
Mr.d0x notes that while this technique isn't entirely new—Zscaler identified its use by malicious gaming sites to harvest Steam credentials back in 2020—the availability of these pre-made Chrome window templates now empowers red teamers to craft convincing phishing login forms. This serves as a valuable tool for assessing the security measures of their clients or teams.
If you're interested in experimenting with the Browser in the Browser phishing attack, the templates are accessible on GitHub.
This video discusses the dangers of fake Google Chrome update pop-ups that can introduce malware to your system.
This video provides guidance on how to eliminate false McAfee virus pop-up notifications that may mislead users into installing harmful software.
Thank you for your interest in this topic!