Understanding the Recent Surge in Cyberattacks and Vulnerabilities
Written on
The SolarWinds Cyberattack Revisited
Recent reports indicate that the infamous Russian-backed group, Nobelium, is back in the spotlight with a new series of cyberattacks. This time, they gained access to an email marketing platform utilized by USAID. The SolarWinds attack, which was one of the most significant cyber incidents in history, previously targeted nine major U.S. federal agencies and approximately 100 American companies. Even months after its detection, the repercussions are still being felt across the cybersecurity landscape.
As detailed by Microsoft, Nobelium is currently running a phishing campaign after seizing control of the USAID account on Constant Contact. This malicious operation has affected around 3,000 accounts associated with government entities, think tanks, consultants, and NGOs. While the United States is the primary target, the campaign has also reached at least 24 other nations. The phishing emails contain links that, when clicked, create a backdoor known as ‘NativeZone’, allowing hackers to access personal data and compromise additional devices within the network.
The first video provides insights into the SolarWinds hack, explaining its implications and offering cybersecurity advice.
Recent Vulnerabilities and Concerns
As we delve deeper into the cybersecurity landscape, several vulnerabilities have emerged recently.
Memory Chip Vulnerability
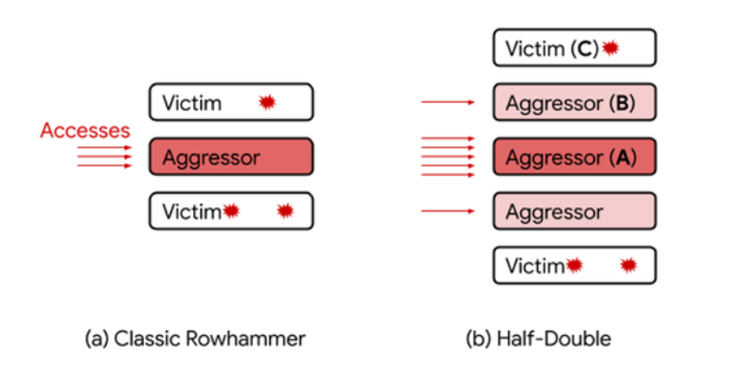
Google’s Project Zero has uncovered a vulnerability known as “Half-Double”, which originates from the Rowhammer issue reported back in 2015. This flaw occurs when DRAM devices repeatedly access a memory row, resulting in bit flips in neighboring rows. Initially, it was believed that such attacks required physical access to the target. However, researchers have now established that these attacks can also be conducted remotely, enabling the compromise of Linux virtual machines in cloud environments. The Half-Double vulnerability expands the original Rowhammer, allowing attackers to influence more distant rows of memory.
Bluetooth Vulnerabilities
A recent analysis by the Agence nationale de la sécurité des systèmes d’information (ANSSI) has revealed that Bluetooth Core and Mesh Specifications are susceptible to impersonation attacks and AuthValue disclosures. These vulnerabilities affect low-energy and IoT devices, as well as large-scale networks. The findings indicate several issues, including impersonation in various protocols and predictable AuthValues that could lead to man-in-the-middle attacks. Users of Bluetooth technology are urged to apply the latest updates from their device manufacturers to mitigate these risks.
Bose Ransomware Incident
In another alarming incident, the Bose Corporation disclosed a ransomware attack that occurred on March 7. It wasn't until April 29 that they determined the attackers had accessed sensitive internal human resources files, including social security numbers and other personal employee data. While the specifics of the ransomware and the attackers remain undisclosed, Bose has since taken measures to bolster its cybersecurity, implementing improved malware protection and collaborating with law enforcement.
The second video discusses how the SolarWinds hack could potentially reshape data security practices moving forward.
Stay informed with the content that matters — Join my mailing list