Phishing Email Analysis: Uncovering the Deceptive Tactics
Written on
Chapter 1: Understanding Phishing Emails
Recently, I sifted through my spam folder and encountered a particularly intriguing email. Today, I want to share my process of dissecting a phishing email that landed in my inbox.

The subject line read, “?????? — GET BITCOIN URGENTLY[???],” which immediately raised my suspicions due to its use of a foreign language (Japanese) and the mention of Bitcoin. This phishing attempt was sent to my Gmail account, allowing me to utilize Gmail's built-in tools to gather more insight about its origin.
To start, I decided to use WhoIs from DomainTools to investigate the domain linked to this email.
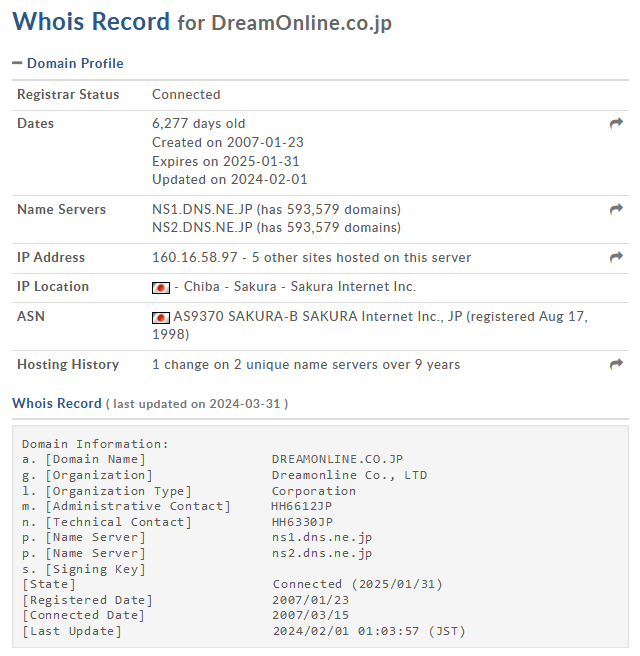
Upon examining the domain, it appeared to be associated with a legitimate email provider, which made it challenging to ascertain any red flags. I then turned my attention to the email content itself, hoping to find some useful information, but my efforts were largely fruitless.

Next, I translated the email to gain a clearer understanding of its message.
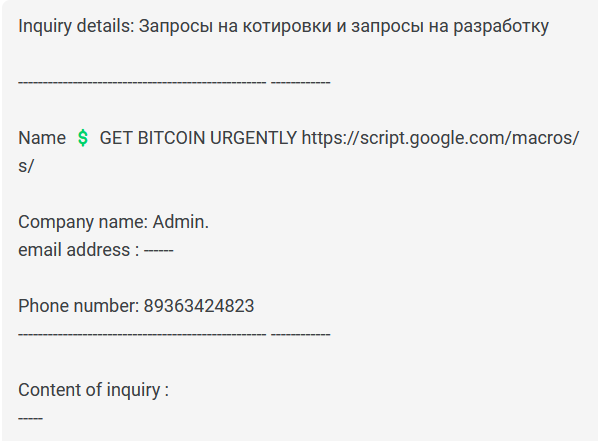
Upon reviewing the translated version, I noticed something peculiar: the email contained text in two different languages, with the second language (Russian) not being translated initially.
So far, the details I gathered about this phishing email include:
- It originates from a Japanese domain.
- It employs the tactic of FOMO (Fear Of Missing Out) concerning Bitcoin.
- It includes Russian text for an unknown reason.
Moving forward, I utilized VirusTotal to check if this email had been flagged previously.
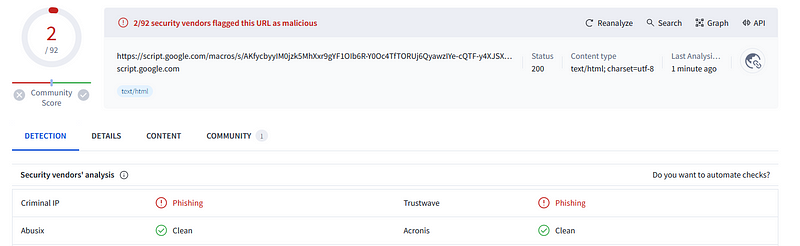
The analysis on VirusTotal revealed that only two security vendors had categorized this as ‘Phishing,’ which is a rather low number.
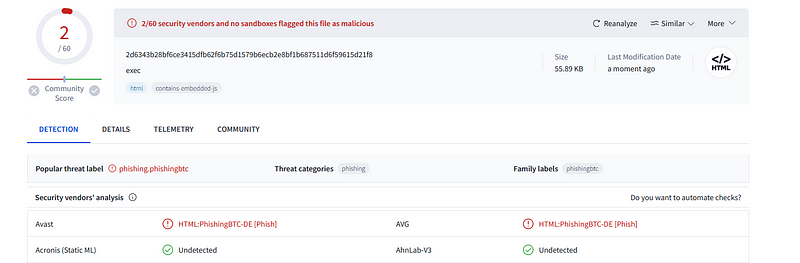
I also ran an executable file through VirusTotal, which provided additional details (SHA-256: 2d6343b28bf6ce3415dfb62f6b75d1579b6ecb2e8bf1b687511d6f59615d21f8).
Next, I turned to URL2PNG to view the associated website without directly accessing it.
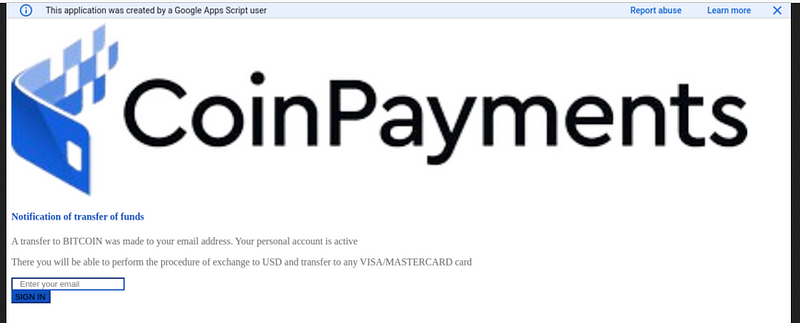
Using URL2PNG allowed me to safely examine the site, revealing that it was not a highly sophisticated phishing attempt. However, it did involve multiple steps to acquire 'my Bitcoin,' indicating that they aimed to collect my email address to gauge my susceptibility.
This experience underscored the necessity of remaining vigilant in today's digital landscape. I hope my analysis is insightful and demonstrates my method for identifying phishing attempts. As these threats grow increasingly intricate, it's essential to remain alert. Always scrutinize unexpected messages, particularly those that request personal information, as this one did by asking me to verify my email address (which I will not do).
Thank you for reading my experience! If you found this useful, be sure to follow me for more similar content.
Chapter 2: Learning Through Video Analysis
In this video, "Phishing Analysis Fundamentals | TryHackMe Full Walkthrough," viewers can gain foundational insights into phishing tactics and analysis techniques.
The second video, "Practical Phishing Email Analysis | PhishTool & Any.Run | TryHackMe," offers hands-on approaches to dissecting phishing emails using specialized tools.