Cybersecurity Alert: Beware of RMM Phishing Scams
Written on
Chapter 1: Understanding the Threat
Cybersecurity experts have issued a warning regarding a phishing scam that employs remote management software (RMM) to deceive individuals and siphon their funds. This advisory comes from the Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA), highlighting a new tactic where attackers trick victims into installing legitimate RMM applications, ultimately granting them access to sensitive financial information.
The advisory emphasizes that the RMM tools being exploited are authentic applications with valid uses, which means they typically do not raise any red flags with antivirus software. This clever strategy allows cybercriminals to bypass standard security protocols by leveraging the legitimacy of the RMM tools, rather than attempting to convince victims to download malware that would alert users to potential threats.
Section 1.1: The Mechanics of the Scam
CISA and NSA have pointed out that while the current phishing campaign is primarily aimed at financial theft, the remote access gained by these attackers can lead to a variety of malicious actions. These can include the theft of personal information like usernames and passwords, the installation of backdoors for unauthorized access to systems, and even the potential launch of ransomware attacks.

Section 1.2: The Phishing Approach
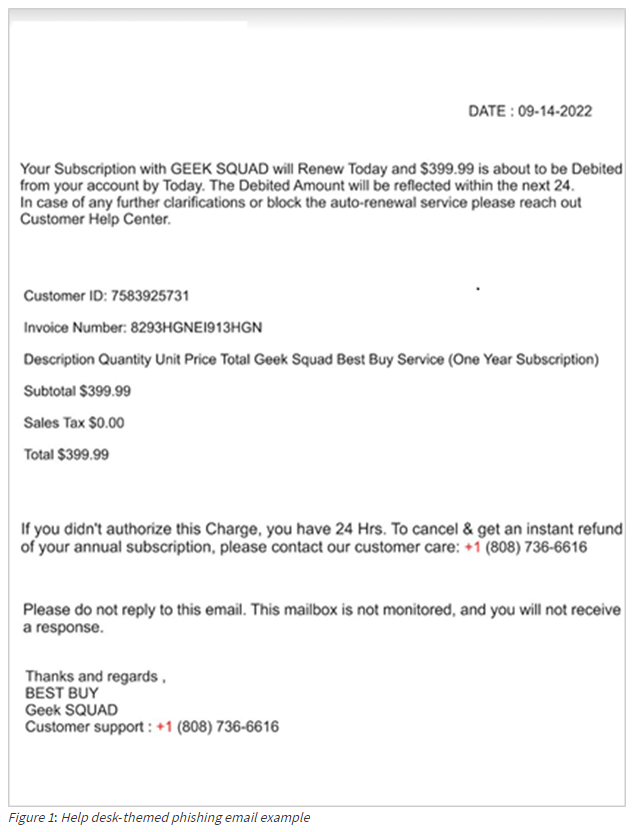
Security analysts believe this operation is being executed by a financially driven cybercriminal group that has been active since June 2022. The attacks typically start with phishing emails designed to manipulate victims. One prevalent tactic involves sending an email claiming that an annual subscription is about to renew at a high price (as illustrated above). This tactic is meant to instill urgency and anxiety, prompting victims to reach out to the “help desk” mentioned in the email.
Once contacted, the scammers masquerading as support staff will persuade the victim to install remote management software to resolve their concerns and cancel the fictitious payment. However, in truth, no payment is due; the attackers' sole intent is to trick the victim into accessing their online banking account while the remote management application is active, enabling the theft of funds.
Chapter 2: Tools of the Trade
The first video, titled "I am a hacker who has access to your operating system," dives into the tactics used by cybercriminals, shedding light on how these scams operate.
Cybercriminals are utilizing tools like ScreenConnect and AnyDesk but can also exploit any other valid remote management software. Moreover, since these attackers can use portable executables of legitimate RMM applications, they can evade both administrative controls and software policy restrictions.
CISA recommends adopting best practices to guard against falling victim to this type of scam. Suggested measures include blocking phishing emails and monitoring network activity for any unauthorized software usage. Additionally, organizations should implement user training and conduct phishing simulations to raise awareness about the dangers of visiting suspicious sites, clicking on dubious links, and opening unverified attachments.
The second video, "Syncro Ask Us Anything / Sep 28, 2023," provides insights into the evolving landscape of cybersecurity and the importance of staying informed.
Stay updated with critical information by subscribing to my weekly newsletter for more stories like this.